Cyber Attack is not the Risk
Reports continue to emerge on a regular basis of cyber-attacks that have impacted Government and private sector organisations alike. Insurance firms now offer policies to protect against cyber-attack and, at one point, the Australian Government even appointed a special advisor to the Prime Minister on cyber security. Not to mention that consulting companies with a specialty in all things cyber are generating revenues, the likes of which have not been seen since the days of Y2K.
But there is a problem, cyber-attack is not a risk, it is a cause. In fact, it is not just the cause of one risk but two:
- Unauthorised release of, amendment to, and/or use of, corporate and/or confidential information stored electronically; and
- Loss of, and/or loss of access to, records stored electronically.
Don’t get me wrong, cyber-attack is a significant issue and I am certainly not downplaying the fact that it has cost business and government organisations alike millions upon millions of dollars.
The purpose of this rant, therefore, is not to try and convince people it is not an issue, but instead to highlight that it is but one of many ways that could lead to the above risks materialising. In fact, with the emphasis placed so heavily on protection against cyber-attack, organisations may be leaving themselves vulnerable to other (more likely) ways that these risks can occur.
So, let’s start with the first of these risks and look at the ways that confidential information can be released to a party/ies that it shouldn’t be. Think some of them are far-fetched, well I have included examples and headlines to demonstrate that they can, and have, happened.
Unauthorised release of confidential information |
|
|
Direct cyber-attack on the organisation from external players |
|
|
Direct cyber-attack on third party storing organisation’s information |
|
|
Unauthorised sharing of system access (log in) information with another party |
|
|
Computer left unlocked when person away from desk |
|
|
Access not removed when employee leaves organisation |
|
|
Introduction of a virus through opening of email attachment, accessing suspicious website or inputting external storage device |
|
|
Introduction of a virus through inputting external storage device |
|
|
Deliberate act by a person who has access to information to release electronically or in hard copy |
|
|
Unencrypted data storage device with confidential information lost |
|
|
Information printed by someone which is removed from the printer by someone without authority |
|
|
Information taken from a person’s desk/work area while unattended |
|
|
Information released (deliberately or inadvertently) by a service contractor’s personnel |
|
|
Inadvertent publication of information on organisation’s website or by email |
|
|
Transmission of confidential information via non-secure means that is sent to the wrong recipient/s (email/fax/mail) |
|
|
Items lost/misplaced during change of office locations |
|
|
Confidential information left in furniture/safes or on hard drives sent for sale/ disposal |
|
|
Files (hard or electronic) lost or stolen while in the possession of a person outside of the office |
|
|
Theft through unauthorised entry into premises |
|
|
Information not disposed of/ destroyed appropriately by rubbish removal contractor |
|
|
Information not disposed of/ destroyed appropriately by member of staff (e.g. confidential information disposed of in standard waste bins) |
|
It is critical, therefore, that we ensure that controls are in place and are effective for all the ways in which unauthorised release of information stored electronically can occur. If we don’t we are not managing the risk in its entirety. Instead, we are focussing on controls for only one of the possible ways the risk may materialise.
The other factor to consider here is the ownership of the risk. I have seen it predominantly being considered an IT risk, however, when we look at some of the causes across those scenarios and the ownership of the controls, it becomes obvious very quickly that this is a whole of organisation Enterprise level risk.
As I covered in Risk Tip # 6 – Managing Shared Risks, the stakeholders involved in the prevention, detection and response to this risk sit right across the organisation as shown in the stakeholder map below:
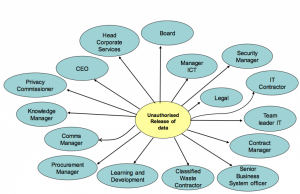
If we move to the second risk, we can see that, once again cyber-attack is a cause – but it is not the only cause:
Disruption to XYZ system for a period exceeding Maximum Acceptable Outage |
|
|
Direct cyber-attack on the organisation from external players |
Cyber attack: NHS paralysed by hackers using NSA tool – The Guardian Australia |
|
Direct cyber-attack on 3rd party managing system |
How Census fail 2016 unfolded – Computerworld |
|
Hardware failure |
|
|
Software failure |
|
|
Deliberate or inadvertent act by an individual inside the organisation |
|
|
Deliberate or inadvertent act by a person at a third party provider |
|
|
Capacity of the system exceeded |
|
|
Access not removed when employee leaves organisation |
|
|
New system implemented with inherent flaws |
|
|
Power Surge |
|
Once again, this is not only an IT risk, but also involves multiple stakeholders, each managing controls that need to be effective to manage the risk holistically.
In summary, you may have the best cyber-security in the world, however, without ensuring the effectiveness of controls associated with all the other ways there can be an unauthorised release of information or a disruption to service, organisations may be leaving themselves exposed whilst at the same time thinking they have the risk ‘in hand’.
Just remember, the biggest leaks in history, Wikileaks, Edward Snowden and the Panama Papers, all of which had global consequences, were not caused by a cyber-attack.
