Am I vulnerable, under threat, or at risk?
I recently received a request to write a blog to clarify the difference between risk and vulnerability.
In a perfect world risk would be looked at holistically and there would be no need for an explanation, but of course, we are still managing risk in silos – not holistically and it is from these silos that this confusion arises.
Let’s start with my definition of a risk:
A possible event/incident that, if it occurs, will have an impact on the objectives of the organisation. What is a risk?
The key here is it is the event that we are trying to stop, for example:
- unauthorised release of corporate/confidential information;
- fraudulent/corrupt behaviour by a member of staff;
- disruption to critical business function for a period in excess of stated maximum acceptable outage; or
- organisation delivers a project or program that is unsafe or not fit for purpose.
Each of these risks have causes and in an ideal world, controls are linked to those causes to minimise the likelihood that the event will occur. Classic risk management.
So, how is this different to being under threat or vulnerable?
In broad terms, a threat is a cause and a vulnerability is representative of control effectiveness. These terms are mainly used in the management of “security risk”. It is the introduction of these terms that causes the confusion.
In the security world threats can include:
- criminal gangs;
- terrorists;
- single actor;
- cyber criminals, different types of weapons etc.
Stating that these threats are risks is actually hindering the management of the true risks.
Let’s look at a classic example – the vulnerability to the threat of a cyber-attack.
Remember, my world – cyber-attack is not a risk, it is a cause. In fact in this example, it is not just the cause of one risk, but two:
- unauthorised release of confidential information; and
- disruption to XYZ system for a period exceeding Maximum Acceptable Outage.
When we capture it as a risk as opposed to a threat, we can then start to develop causes and controls as shown below:

In this case, the “threats” are the causes – but they are causes for a broader risk. If we then went on to assess the effectiveness of the controls, we can then assess our level of vulnerability to the identified threat/cause. If we rate our firewall technology as being ineffective then the organisation has a vulnerability to cyber-attack (the threat/cause) which heightens the likelihood that the risk (i.e. unauthorised release of confidential information) will materialise.
It is also the case in relation to physical security. We see organisations assessing the threat of terrorism, the threat of theft, the threat of wilful destruction of property, the threat to personnel etc. But once again – I believe the focus is all wrong. We need to be assessing the risks.
Unlike in the previous example where the threats were causes, when it comes to physical security, the threats are a combination of causes (terrorism) and consequences (theft, wilful damage).
So, what are the risks?
To me, there are a number:
- unauthorised access into/onto premises after hours (in this case the theft, damage, or assault could be potential consequences – but what we are trying to stop is the person with whatever intent they have gaining access)
- assault of a member of staff whilst conducting their duties;
- incident involving Issue Motivated Person or Group (IMPG) at organisation’s site.
Like the previous example, there are causes with controls linked to those causes, which, when assessed for effectiveness, determine the likelihood of the event.
Let’s take unauthorised access into/onto premises after hours as the example:
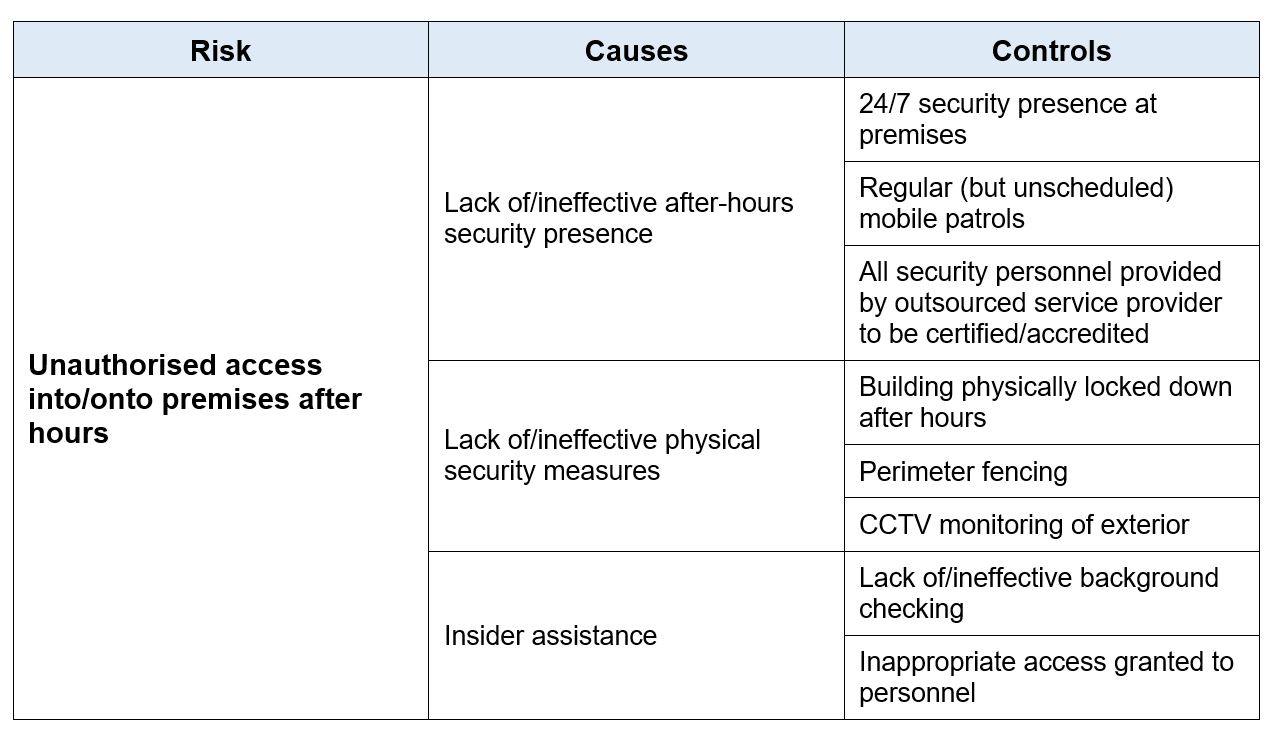
The point I am trying to make? As I have said in a previous blog – there is no such thing as a safety risk, or a security risk, or a reputation risk – they are just risks. Adding terms such as threats and vulnerabilities into the mix encourages risks to be managed in silos – not holistically and you run the risk of being distracted by a threat and vulnerability, when the main game, is to:
Manage the risk – not the cause.
Learn more about risk management – find a course to suit you!
